# show sessions or # monitor session gives you a whole statistics of active sessions on your session director.
What to do if you want to see the number of sessions on each session-agent? Use # show sipd agents
This extremely useful command can help you to destinguish the suspiciously high (for your network) connections count on a concrete session-agent. And you will see the problem agent while being DDoSed or under real high load. Or just see sessions per session-agent.
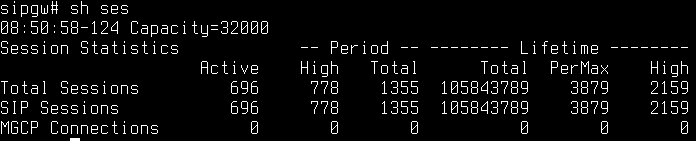
# show sessions
The left column shows the number of active sessions on your Session Director. The right one demonstrates the highest number of sessions ever been on SD:
This is how # show sipd agents looks like:
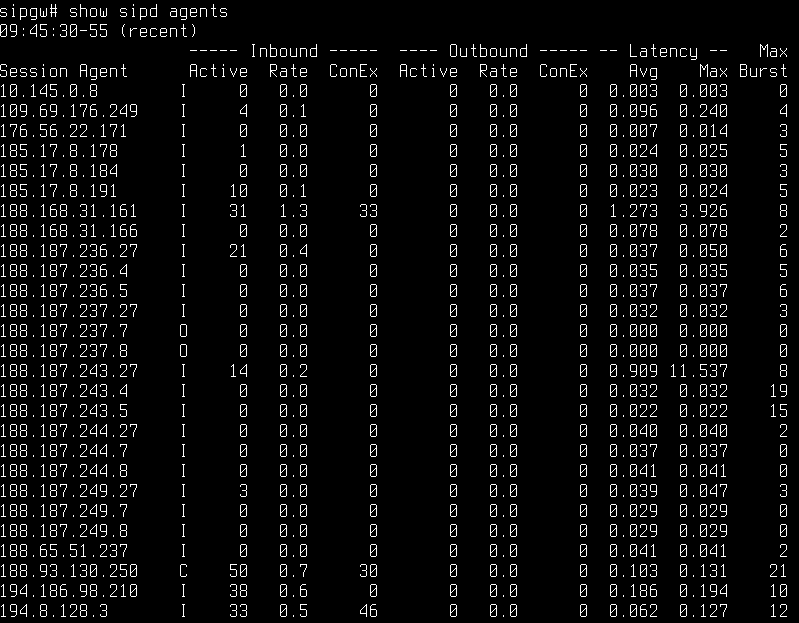
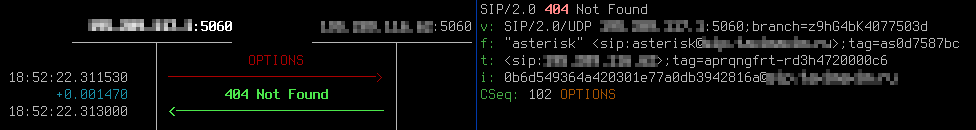
The letter I in the second column means that the session agent is ‘in service’.
The letter O means that it’s ‘out of service’, unused.
The letter C means that constraints are configured and are used right now: the number of sessions is higher than allowed. The ‘Active’ column shows the number of sessions. The column ‘ConEx’ is ‘Constraints exceeded’ – the number of ignored due to the limitations sessions for the last 100 seconds.
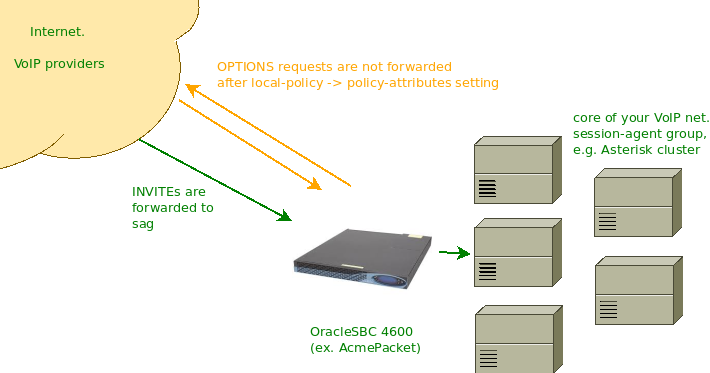
As you can see, session-agents may be inbound and outbound. In this example we see only inbound, they are peers with SIP providers. The outbound are peers with Asterisk nodes in the core of the network, they also have such statistics.
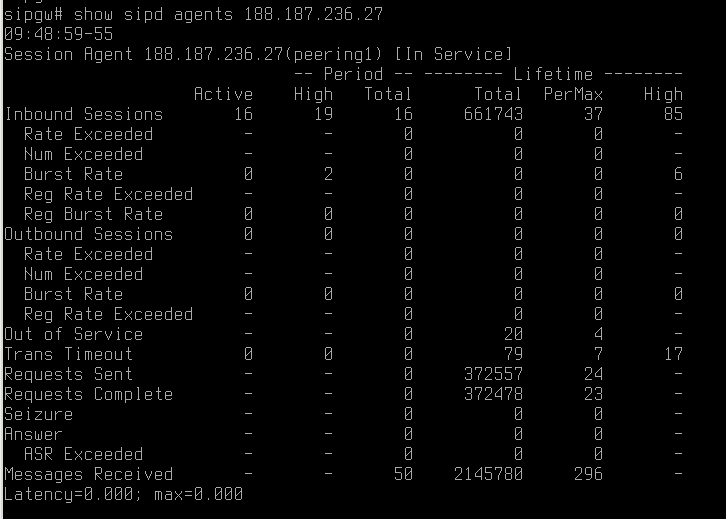
It is possible to see a detailed statistics for any of the configured session-agents:
# show sipd agents %ip address% or # show sipd agents %session-agent name%
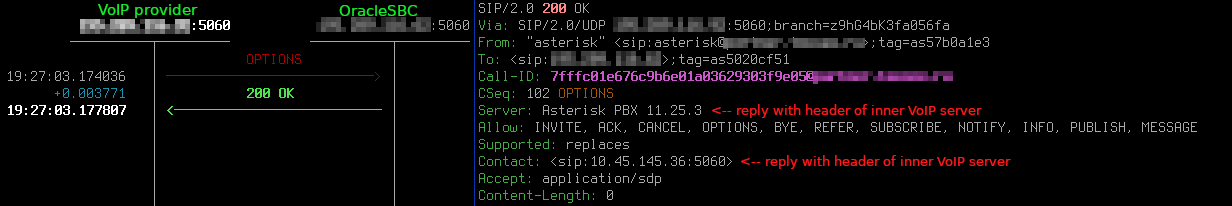
Have a look at session-agent which is marked with I letter (in service):
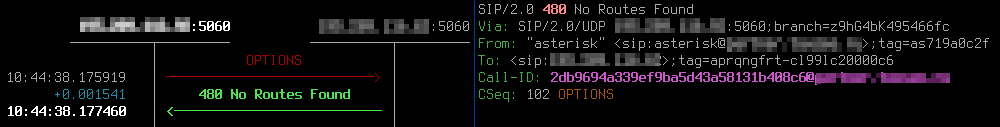
And one more example for the session-agent with ConEx – constraints exceeded:
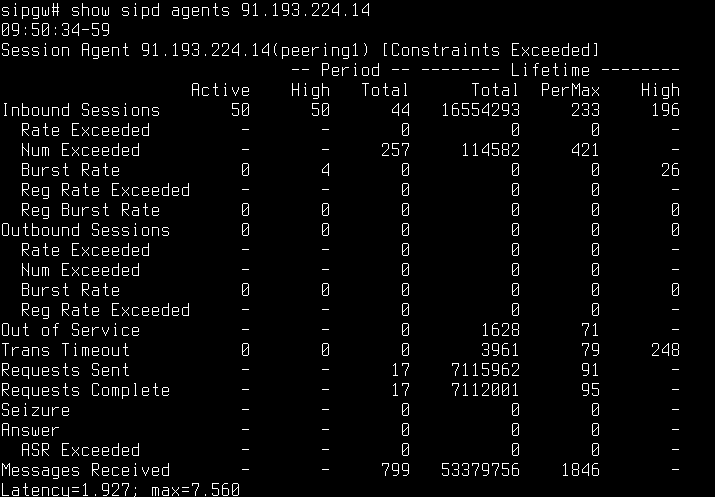
Constraints can be configured either in # configure terminal -> session-router -> session-constraints and then applying them variant_1) on the sip-interface (# configure terminal -> session-router -> sip-interface -> constraint-name), variant_2) on a realm (# conf t -> media-manager -> realm-config), or for the session-agent directly.
Here’s an example of a directly applied (but disabled) constraint on a session-agent:
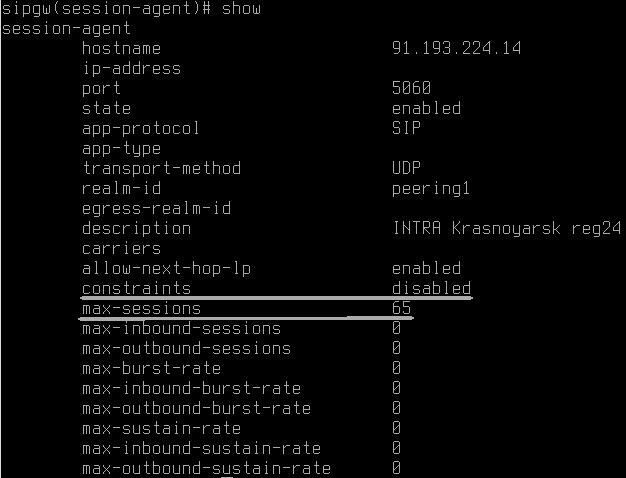
Just be sure to set ‘constraints enabled‘ in your session-agent, not only the value, otherwise they will not be applied.