First of all, a nice PDF with a bunch of useful links: https://supportforums.cisco.com/sites/default/files/legacy/0/8/6/41680-SPA_DocsMap_012711.pdf
1. There are two ways of provisioning:
– using TFTP/FTP/HTTP server and pushing it’s address with the DHCP option, in case of using DHCP server in your network. In this case the phone will try to download the configuration/firmware from the server specified during the next reboot. But we need to reboot phones forcibly after that.
– without using DHCP server and dhcp-options. Just telling the phone with a direct HTTP request the URL path of config file/firmware to load, either from browser, or from Linux console, using curl. In this case the phone reboots automatically to apply the newly downloaded config/firmware (if there is an active call, the phone waits for its end and only then reboots to aply config. But I haven’t tried to upgrade firmware during the active call).
Download the archive with firmware, unpack it and rename the firmware file from something like spa50x-30x-7-4-9c.bin to spa.bin.
Next, we need some server, e.g. a small simple HTTP server weborf.
After installing, run it, specifying the directory with spa.bin file:
weborf -p 8000 -b /home/lexus/downloads/spa_303_firmware_7.5.5/
If there is Python installed on your machine, you may use its built-in http-server, running this command from a directory with spa.bin:
python -m SimpleHTTPServer 8000
Remember that it’s not always possible to skip firmware releases, for example I tried:
– 7.5.2 —> 7.6.1 – unsuccessful
– 7.5.2 —> 7.5.5 – OK
– 7.5.1 —> 7.5.5 – unsuccessful
– 7.4.9c —> 7.5.5 – unsuccessful
– 7.4.9c —> 7.5.1 – OK.
Read below how to upgrade the firmware.
2. Let’s imagine, we need to change the configuration of a phone. We need to disable the Call Forward feature.
First of all look through the XML-config file of a working phone: http://phone.ip/admin/spacfg.xml
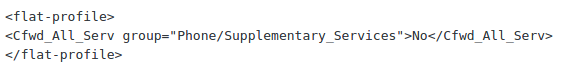
To disable CallForward feature we need to change this parameter from ‘Yes’ to ‘No’:
![]()
Tip: all XML parameters are called the same way as in the web-interface, but with underscore instead of spaces
Create the spa303.cfg text file in your web-server directory:
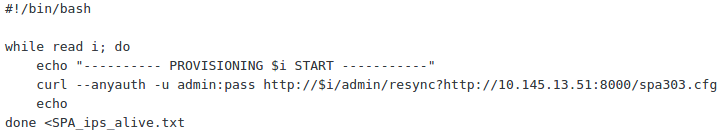
And now tell the phone using curl to apply it:
curl --anyauth -u admin:pass http://phone/admin/resync?http://websrv.ip:8000/spa303.cfg
3. You may also provision phones from web-interface:
http://phone-ip/admin/upgrade?http://10.145.13.51:8000/spa.bin http://phone-ip/admin/resync?http://10.145.13.51:8000/spa303.cfg
… but this is not true way :) .
It’s much more cool to do everything with curl:
curl --anyauth -u admin:pass http://10.145.13.232/admin/reboot curl --anyauth -u admin:pass http://10.145.13.229/admin/upgrade?http://10.145.13.51:8000/spa.bin curl --anyauth -u admin:pass http://10.145.13.229/admin/resync?http://10.145.13.51:8000/spa303.cfg
… they say, it’s also possible to use ‘–digest’ option in curl, but I haven’t tried, as ‘–anyauth’ works fine.
Tips and Hints:
Assuming you’re using ISC-DHCPD server:
host spa303-1353 { hardware ethernet 3c:ce:73:d3:f9:dc;
fixed-address 10.145.14.103; }
host cisco303-1354 { hardware ethernet 3c:ce:73:d3:e9:e4;
fixed-address 10.145.14.104; }
…and need to get all phone IP addresses from its config. Do:
grep -A1 spa dhcpd.conf | grep -vE '^#' | grep fixed-address | grep -o '[0-9]\{1,3\}\.[0-9]\{1,3\}\.[0-9]\{1,3\}\.[0-9]\{1,3\}'
grep -A1 cisco dhcpd.conf | grep -vE '^#' | grep fixed-address | grep -o '[0-9]\{1,3\}\.[0-9]\{1,3\}\.[0-9]\{1,3\}\.[0-9]\{1,3\}'
… and create a text file SPA_ips_from_dhcp.txt .
But DHCPd config may contain records of non-existent phones, that’s why we need to check if the IP addresses are real network devices (that they reply to OPTIONS SIP-requests), and these devices are Cisco and/or Linksys phones (useragent is Cisco… or Linksys…).
We’ll use sipvicious tool for that (make sure to have Python installed to run it):
python svmap.py --inputtext=/home/lexus/SPA_ips_from_dhcp.txt | grep -i SPA | awk '{print $2}' | sed 's/.....$//'
… and write this list to SPA_ips_alive.txt .
Now it’s time to provision the actual list of IP-phones with the script: