One more post about INVITE rejecting.
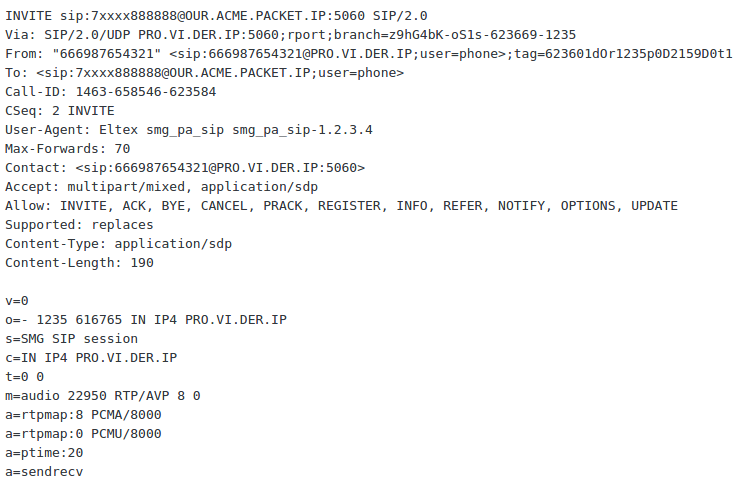
The task: reject malicious SIP traffic coming from some country to our number. All INVITEs contain a From: header with 12-digits number starting with 666. The may also contain a plus sign at the beginning or 810, or +810.
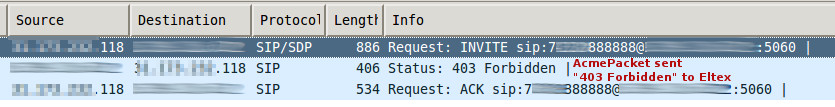
It is also important to set a ‘new-value’ parameter, containing a status code and SIP description (in form of “Code:Description”), as some (or maybe most) PBXses/softswitches/proxies go on sending INVITEs if we just do ‘action reject’. After answering from AcmePacket with something like “403 Forbidden” the remote side stops sending endless INVITEs to AcmePacket.
Part of sip-manipulation:
header-rule
name dropHACKERS
header-name From
action manipulate
comparison-type pattern-rule
msg-type any
methods INVITE
match-value
new-value
element-rule
name dropHACKERS1
parameter-name From
type uri-phone-number-only
action reject
match-val-type any
comparison-type pattern-rule
match-value 666[0-9]{9}$
new-value 403:Forbidden
This is how it looks like after rejecting malicious INVITE with “403 Forbidden”: