Preface: the PIKE module itself blocks SIP requests (just stops sending any replies) in case of flood. This article is about going on – adding flooding IP addresses to ipset for further rejecting any traffic to the OpenSIPS server using iptables.
1. Create an ipset with auto removing addresses after 120 seconds and ability to add comments.
ipset create SIPFLOOD hash:ip timeout 120 comment
2. An iptables rule, which will drop incoming traffic from src IP addresses from created ipset table:
iptables -A INPUT -m set --match-set SIPFLOOD src -j DROP
3. Allow OpenSIPS’ run-user (usually ‘opensips’) executing ‘ipset’ command without a password (add this line to /etc/sudoers using ‘visudo’ command):
opensips ALL= NOPASSWD: /sbin/ipset
4. OpenSIPS configuration.
Part of modules section of config:
#### exec
loadmodule "exec.so"
#### antiflood module
loadmodule "pike.so"
modparam("pike", "sampling_time_unit", 2)
modparam("pike", "reqs_density_per_unit", 10)
modparam("pike", "remove_latency", 120)
Part of OpenSIPS script, assuming that somebody sends us too much OPTIONS requests:
if(is_method("OPTIONS")) {
pike_check_req();
switch($retcode) {
case -2: # detected once - simply drop the request
exit;
case -1: # detected again - ban the IP and drop request
exec("/usr/bin/sudo ipset -exist add SIPFLOOD $si");
exit;
}
sl_send_reply("200", "OK");
exit;
}
5. You may test all this with ‘sipp’ tool.
This is for generating 10 requests (-r) in 2 seconds (-rp 2000) and exiting sipp after sending 10 requests (-m):
sipp 172.16.0.222 -r 10 -rp 2000 -m 10 -sf OPTIONS.xml
This – for generating 70 requests (-r) in 2 seconds (-rp 2000) and exiting sipp after sending 70 requests (-m):
sipp 172.16.0.222 -r 70 -rp 2000 -m 70 -sf OPTIONS.xml
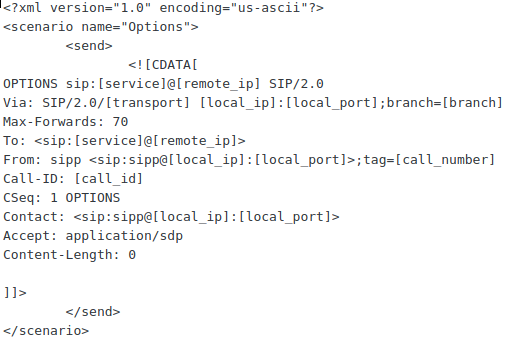
The OPTIONS.xml is as follows:
UPD 2019-july-30: pike writes log messages (at least in automatic mode, but I’m sure that also in the manual ):
Jul 30 06:59:05 ... /opensips[15531]: PIKE - BLOCKing ip 46.166.151.117, node=0x7f6dec201c08
Jul 30 06:59:05 ... /opensips[15533]: PIKE - UNBLOCKing node 0x7f6dec201b38
Jul 30 06:59:07 ... /opensips[15531]: PIKE - BLOCKing ip 46.166.151.163, node=0x7f6dec201d40
If you do not need all these messages (in case of SIP flood it may be too many), just set the log_level for pike.so module:
modparam("pike", "pike_log_level", 3)
And then set the log_level for your OpenSIPS to be not so verbose (pike’s log_level must be greater than global):
opensips-cli -x mi log_level 2
… or/and in config file:
log_level=2
